Protecting Your Data And Privacy with Robert Fleming


Data theft has run amok, and the internet is fraught with vulnerabilities. Anytime you are on the internet, you’re putting yourself – and your important digital files and folders – at risk to potential attack. Users should pay close attention to suspicious email, and check frequently to prevent hackers from gaining access to home or business networks.
Malware, spyware and keylogging attacks are real, and can cause significant damage. In fact, research firms tell us that a successful attack can likely cause a small business to close its doors within 6 to 9 months of the attack.
Robert Fleming, founder and president of BlackSquare Technologies, talks about securing your digital information from potential harm through hardware encryption tools. He also shares one of their key tools called Enigma, which delivers secure, simple, real-time USB hardware encryption and decryption to protect data, no matter where that data is stored.
Protecting Your Data And Privacy with Robert Fleming
This is an episode where we are doing a return podcast with Bob Fleming. He’s the Founder and President of BlackSquare Technologies. In the previous podcast, we were talking about the Enigma device. It looks like a thumb drive, but does not store any data. Enigma offers a female connector which allows the user to connect any type of USB storage device. The whole idea is we wanted to get an update as to where we are. If you would, Bob, recap your business and who you serve.
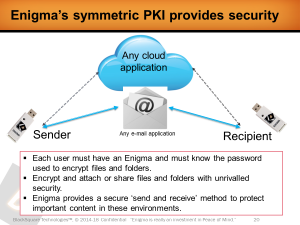
Thanks for having me back, Bob. We’re a small Colorado based company called BlackSquare Technologies, and we build an external hardware encryption tool that we call Enigma. Enigma allows the connection of any USB storage device. Enigma itself does not store data and acts as a firewall to protect against malware and spyware attacks.
With a simple click, Enigma allows the user to encrypt and decrypt data, no matter where that data may be stored. Enigma has been designed to support the consumer and small business, and offers value to a single user to hundreds of users.
It’s also important to mention that Enigma does not have a back door, so please record your passwords.
As we look at the device, let’s back up a little bit and talk about some of your background and how you brought your background forward into the design and bringing to market of this device.
I bring over eighteen years of data security expertise and consultancy experience to BlackSquare. Prior to founding BlackSquare, my colleagues and I worked for a very large storage manufacturing company here in Colorado, where we designed and marketed full disk encrypting and self encrypting hard drives.
In the early 2000’s, I realized myself that data was suspect. If important data fell into the wrong hands, it could be leveraged or monetized against that company, it’s leadership, its board, its investors, vendors and contacts.
My team and I decided that we could design and build a product which will allow us to protect our important data from everybody. That’s how it came about.

I have an Enigma device here in my business. We were backing it up and I have a relatively large backup drive, which has a USB plug on it. It plugs right into Enigma. It’s a very simple process to drag and drop a file and encrypt it. You drag and drop it to the same place. You choose to encrypt or decrypt as you see fit. Some of the things that we talk about here, for folks who are going, “I’m migrating from storing information on my local hard drive to Dropbox or any various cloud providers.” Let’s dig into that process and your thoughts on protecting the data in the “cloud.”
While storing data in the cloud is beneficial, cloud storage is just as suspect as any other form of storage. If an attacker has gained access to your credentials, they now have leverage. So, if you have been breached, no matter where you may store your data, that data may be leveraged.
It’s the cloud provider’s responsibility to securely deliver your data into your cloud account. Once that data is now resident in your account, it’s your responsibility to protect your data.
If you were to encrypt data on your computer using our Enigma, your job is now very easy. If you’d like to send that encrypted data into your cloud account, the data is sent and resides inside our hardware encryption packets, so it’s secure, no matter who might intercept the data.
Enigma also offers ‘trusted user’ symmetric encryption. If I sent an email with an encrypted file, the recipient will need an Enigma, as well as knowledge of the password that I used to encrypt the file.
Enigma is a two factor authentication tool: there is the physical Enigma tool, as well as the password I have used to encrypt data.
If a thief stole my computer and my important digital files and folders were encrypted, there is no way for the thief – or a counterpart – to ever decrypt those files.
When I think about this particular device, how is it different than some of the off-the-shelf ESETor Norton or Kaspersky?
Great question…ESET offers software encryption which resides on the computer. Norton and Kaspersky offer network security options to help the user determine if a web site or an e-mail may be suspicious.
These are software applications which live on your computer and peripherals. Note that all software apps ask the user if they can provide updates and patches to the existing software revision.
There are USB storage devices which provide onboard encryption.
If a hacker has been successful gaining access to your credentials, you are in danger. This vulnerability is a clear and present danger, so manage your data and your credentials accordingly.
 Protecting Your Data: If you think you haven’t been hacked, you’re not paying attention.
Protecting Your Data: If you think you haven’t been hacked, you’re not paying attention.
Would that device also encrypt the data that you send to the cloud or just to that device?
The more expensive IronKey devices may allow this.
Talk a little bit about BitLocker and the challenges or the differences between what you do and what BitLocker does.
BitLocker is a free product that comes from Microsoft. To feel comfortable with BitLocker, select a browser and ask, “How easy is it to decrypt BitLocker? You’ll find hundreds of links. If you’re managing a lot of important digital information, and your firm experiences a breach, you may wish to supplement your data protection strategy.
Like every other file, the larger the file, it takes a little longer for it to encrypt or decrypt. It’s just a function of physics. We were doing some files and they weren’t that big. It didn’t take any time to get those done. I remember years ago, some guy told me there are two types of folks in the world, those that have been sued and those that are going to be sued. In our world, there are those that have been hacked and those that are going to be hacked at some point.
A few years back, I was on a panel with Larry Ponemon, the CEO of Ponemon Research. Bottom line, in these last few years, he’s been heavily involved with IBM and developing a cost of data breach, or CODB. Larry and I were on this panel and we introduced ourselves. I said, “By the way, Larry, what are your thoughts on data breaches?” His response was, “if you think you haven’t been hacked, you’re not paying attention.”
It’s much clearer now in my mind because in any conversation we have, data theft is THE white elephant in the middle of the room. People are always interested in learning what solutions others employ to protect data. Whether they do anything to protect their important data is another matter entirely.

For us, it was a very simple process to get this done. As far as having the device, you’ll need to have the Enigma device. Add to Enigma a USB storage device, whether it’s a thumb drive or a backup drive or some USB source. Now, it’s really simple. It’s very apparent which files are encrypted and which ones are not. Enigma is only visible when it is connected and has been authenticated by the user. When you look across the number of clients that have started using Enigma, who is your prototypical client?
Originally, we built Enigma for the consumer and the small business owner. You’ve seen the tool work. You have one; you know that when you encrypt a file, Enigma encrypts that file in real time. All of the encryption takes place internally, which eliminates various forms of attacks.
Consumers and SMBs expect Enigma to be simple to use. As a user, I want it to be simple too. Or, if it’s not simple to use, no one will use it!
The next step up is larger businesses with more than 100 users. In this environment, Enigma will be used by the owners, the management team, leadership and authorized users in multiple departments. It’s likely that the firm will also provide Enigma units to outside counsel and other contributors who are authorized to gain access to the important data and the company.
Whatever you have needs to be protected.
If I’m a malicious individual or a person and I’m familiar with CryptoBlocker personally. They show up and they managed to get onboard your computer and you’ve encrypted your files. What do they see or what can they do?
Great question. I have already encrypted what files and folders are important to me. I make a mistake, and allow an attacker access to my data. The hacker may attempt to encrypt my data and then leverage that data.
Because I have educated myself and have chosen to encrypt my data, there is a very high probability that I have backed up my data in a number of locations, some online, some offline.
Bottom line is that I’ve done what I can to protect my data and my network.
Because I have backups, I won’t have to pay any ransom, but I do need to share with others that my network experienced a breach.
That makes that pretty straightforward. When you have a typical response from the client or potential client with some of the things. Let’s say that I’ve encrypted files and done all of these things and then somehow, I lose the Enigma device. What happens?
Losing an Enigma is a straightforward proposition – just order a new Enigma. Now, log in using your password. So, in about 3o seconds you are ready to go.
We always recommend that users write down their passwords. If you haven’t and forget your password, that data will remain encrypted until you remember that password.
I suggest paper and pencil because an attacker would literally have to break in to your office to gain access. This is a rare occurrence today as opposed to a hacker gaining access via your router or modem or thru malware.

If you write it down and you’re at home or somewhere, you have a locked drawer or safe or they got to know where to look and where to find it. That covers that part. You can take and encrypt your cloud data, which we talked about. The speed of the device, do folks ever ask you about encryption speed?
As a USB tool, Enigma reduces the overhead to encrypt or decrypt files and folders. Enigma will encrypt or decrypt, based on the size of the file…it will take a bit longer to encrypt a gigabyte of data as opposed to a ten megabyte file.
It’s one of those things in the scheme of things. Nowadays, we seem to take in and have more gigabyte files. I can remember when all the storage you had wasn’t a gig, but that’s a few years ago. For you, the progress since the last time we’ve talked, the product is getting out into the marketplace. What’s been some of your feedback from some of your user-base?
We’ve done a great job of building the tool, and we’ve spent the time to become certified by FIPS, a regulatory body under the auspices of NIST.
Our passion is making sure it’s simple and it works all the time. We support our customers in the event they have questions, and continue to commit to improve our products.
Be the guy that steps forward when they said to stand still.
I think it is the point. It’s a two-step.
Remember that we as users have progressed in using computers over the years. Using an Enigma allows the user to secure files and folders, but it requires an extra click!
We talked about that too. Let’s say that you have sensitive files and you put them in a folder. You can take and encrypt the folder in mass. You can decrypt the folder in mass. It’s a mechanism to take care of that particular case. If you don’t care about the picture of your cat, that’s not a problem; just don’t encrypt it. If you have a series of sensitive files, if you’re doing financial stuff at home with Quicken, you can take and make sure that that particular group of files is encrypted. That makes it fairly simple.
Simple is expected nowadays. The typical user will create one password for Enigma, and encrypt all of the files that are important, sensitive, or critical. That’s great.
Enigma users identify with this mindset, as opposed to the mindset that says, “I’m going to hope and pray.” If you have been hacked, and we know that this is very likely, do you have a recovery plan?
Network security professionals focus on creating and managing policies to protect users and the network as a whole. Why? To protect the company’s assets.
Ultimately, network security efforts are created to protect important, critical and sensitive data. Let’s make sure that the data is encrypted and protected whether the attacker comes through the network or tricks a user to click on a sneaky e-mail.
For the folks that are going, “I am interested and need to know more.” How do they find you on social media?
We’re easy to find. It’s BlackSquare Technologies. You can do Info@BlackSquareTechnologies.com. You can go to our Facebook site. You can find us.
Shifting gears a little bit, a book that you’ve gone through or looked at that helped you run your business or adjusted your perspective? For me, I was looking at Agile StrategyIt’s a book from research out of Purdue. It talks about incremental pieces of 30 days and 90-day pieces. That’s been a good piece for me. Looking at your timeframe and working with BlackSquare, we all hear about the good stuff when things work. Was there an instance where things didn’t work out quite as well that set the stage for the success that you’re enjoying now?
Yes indeed; it takes time to build a simple yet secure product. We originally started with a concept to secure data. We continue to improve our solutions by innovating and developing better ways to secure and protect data in multiple environments.
The chipset technology that you have in this thing, it’s really robust, isn’t it?
Yes, it is. It’s very capable. There’s no latency. When you instruct Enigma to encrypt the data, it doesn’t have to wait for the operating system. It doesn’t have to ask the CPU. It doesn’t have to ask the software app. It says, “Yes, sir. It’s done,” in real time.
It’s a real benefit.
Convenience is what it boils down to. It’s all about convenience, and security.
I think about the convenience factor and it’s also a habit. We’ve all gotten to the point, by and large, you don’t leave your car running at the 7-11. There’s a reason. You don’t leave your car running out in front of your house. There’s a reason. You think about this as one more step in your protocol. The internet’s a wonderful place, but it also has some bad actors.
 Protecting Your Data: You need to record your passwords because it’s like a safety deposit box. Even if the bank has their key but if you don’t have your key, you’re not getting in.
Protecting Your Data: You need to record your passwords because it’s like a safety deposit box. Even if the bank has their key but if you don’t have your key, you’re not getting in.
Data security should be a priority. If you’re using your computer currently to develop a spreadsheet or a Word document or another project, you may not need the internet to do that. So, why not disconnect and remove that risk?
Only use the internet when necessary. There are people out there that say, “When I go to lunch, I turn off my computer. When I get back from lunch. I turn it back on.”
What’s the old statement they say about paranoia? “Just because you’re paranoid, it doesn’t mean they’re not out to get you.” If you could put an ad on page one of the local paper sharing your message, what would it say and why?
We’ve looked at messaging for our product because it solves a problem. Enigma encrypts important data. We’ve worked hard to develop messaging; finally, someone said, “If it’s important, encrypt it.” It makes sense. If we talk about the various market sectors, not one doesn’t want or need to protect important data.
What are the most vulnerable market sectors? Healthcare, Finance, Professional Services and Pharmaceuticals.
Serious breaches have occurred in all of these sectors.
Wouldn’t it be great to say, “We experienced a data breach, but all of our important data was indeed encrypted or protected.”
That reads better on the front page of the newspaper.
Yes it does. It also provides a level of confidence to your customers, vendors, leadership, investors and colleagues.
If you want to succeed, you’ve got to make it happen.
If you were to look back over the past year or so since we visited the first time through here, the best allocation of time or initiative that’s helped the company from that point to here, where would you say you used your time best?
We’ve updated our Windows products as well as introduced a Mac product to great reviews.
For you, if somebody said, “What’s your most unusual habit or what others may consider out of the ordinary that’s helped you with BlackSquare the most?” What would that be?
We want to ‘get it right’ so that our users see value. Getting it right is a 24/7 commitment.
That’s a typical entrepreneur for sure. For you, if you were going to offer advice to a new president or CEO that’s stepping into the role as you have, what advice would you offer to them?
Surround yourself with knowledgeable people who get what you want to accomplish, and aren’t afraid to suggest different ways to accomplish the objectives.
What are misconceptions about your role as the Founder and President of Enigma and BlackSquare?
In a small company each member wears a lot of hats…nothing new here, Bob.
Looking back over the past few years, what would or should you have said no to and why?
Building a business from the ground up isn’t for everybody. And, not everyone is ready to abandon security for the challenge to build something great.

We didn’t even touch on that. Do you want to touch on the price point for this device?We offer two Enigma price points: Enigma has a retail of $169.95, which includes a one-year update subscription.We also offer an Enigma and the subscription, along with a Sandisk 32Gb USB thumb drive. This retails for $199.95.
Is there a quote that you find meaningful or one that you use frequently?
Yes; in today’s world, “If it’s important, encrypt it.”
If I was to talk to the colleagues and the folks that have worked with you on this, what would they say that you’re best at? How did you utilize that to help develop and bring Enigma to the market?
I like to listen to folks to learn. If we can help, I volunteer. I work with very technically astute folks, including CISOs, CSOs, and CISSPs, whose job is to evaluate products and protect networks.
You’ve got to go make it happen. You’ve got to expose the product. You’ve got to promote the product and the company. You’ve got to develop that reputation. We want the reputation to be sterling.
Bob, I appreciate you stopping by and doing this update on where Enigma is with BlackSquare Technologies and the progress since the last time we’ve talked. Thank you so much. I look forward to hearing of your success.
Thanks, Bob. We’ll be back soon for round three. Thanks.
Links Mentioned:
- BlackSquare Technologies
- Bob Fleming on a previous podcast
- Ponemon Research
- Info@BlackSquareTechnologies.com
- Facebook – BlackSquare Technologies
- https://youtu.be/E4fmk-2Y760?t=8
- https://www.BlackSquareTechnologies.com/
About Robert Fleming

I have been in the data security field for close to 19 years now, and have observed aa huge increase and frequency in data theft over that time. Moreover, we’ve seen data theft come into its own over the past 5 years; hackers and bad actors have stolen not only money but valuable and confidential data, surpassing trillions of dollars. Thieves access, monitor and then monetize data. Once ‘in’ a network, it’s very difficult to remove their presence.
The genesis of BlackSquare came about by thinking we could build a simple yet secure ‘tool’ that any user could manage to encrypt and decrypt data. That was the idea; it has to be simple to manage and simple to use. Why? We wanted to build this product so that consumers and SMBs could now manage data independent of the operating systems. As you know, both WIN and MAC operating systems are continually under pressure to fix problems, which may be an entry point for the hackers and bad actors.
After developing a skeleton concept, we did quite a bit of market research to make sure we were on the right track, to validate what we needed to build0 and to see if there was a market out there. Well, it turns out that the market is global; that millions of users are looking for a way to protect their valuable data.
Love the show? Subscribe, rate, review, and share!
Join the Business Leaders Podcast Community today:
- businessleaderspodcast.com
- Business Leaders Facebook
- Business Leaders Twitter
- Business Leader LinkedIn
- Business Leaders YouTube
The post Protecting Your Data And Privacy with Robert Fleming appeared first on My podcast website.